Uncovering Android Vulnerabilities: Microsoft’s Proactive Approach
In a recent cybersecurity endeavor, Microsoft’s research team unearthed a vulnerability pattern within several widely-used Android applications. This discovery revealed a path traversal flaw that could potentially allow a malicious entity to overwrite files in an app’s home directory. The severity of this issue is underscored by the fact that it could lead to unauthorized code execution or token theft, thereby granting attackers extensive control over an app’s operations or access to a user’s sensitive data and accounts.
Microsoft’s vigilant approach led to the identification of multiple affected applications on the Google Play Store, cumulatively surpassing four billion installations. The company’s initiative to share this information aims to encourage developers and publishers to scrutinize their apps for similar vulnerabilities, rectify them, and avert such risks in future updates. Microsoft’s commitment to cross-platform security is evident as they continue to collaborate with the security community, sharing insights and threat intelligence to bolster user protection.
Upon detecting the vulnerability, Microsoft engaged in a responsible disclosure process, reaching out to the developers of the affected applications through their Coordinated Vulnerability Disclosure (CVD) and Microsoft Security Vulnerability Research (MSVR) programs. The security teams at Xiaomi, Inc. and WPS Office were among those who responded promptly, investigating and resolving the issues. Microsoft advises users to keep their devices and apps updated to benefit from these security fixes.
To further raise awareness and assist developers, Microsoft partnered with Google to publish an informative article on the Android Developers website. This collaboration is a testament to the shared commitment to application security and the importance of industry partnerships in addressing cybersecurity challenges.
Microsoft’s blog post serves as both an educational resource and a call to action, providing a general overview of the vulnerability pattern, with a particular focus on Android share targets. The post includes a case study demonstrating the potential impact of such vulnerabilities, extending beyond the confines of a mobile device to potentially affect local networks. Microsoft’s guidance for users and developers highlights the collective responsibility in enhancing security.
Understanding the Android Ecosystem’s Security Measures
Android’s architecture is built on the principle of application isolation, assigning each app its own data and memory space to ensure secure data and file sharing. The content provider component plays a pivotal role in this ecosystem, serving as a secure interface for data management and exposure to other apps. The Android SDK’s
Each file provider is identified by an
Common Implementation Missteps
While the content provider model offers a secure file-sharing mechanism, issues arise when consuming applications fail to validate file content or trust filenames provided by serving applications. A malicious
Share Targets: A Closer Look
Share targets are apps that handle data and files sent by others, including mail clients, social networks, and file editors. The Android share-sheet dialog facilitates user selection of the destination app for file sharing. However, a malicious app can bypass this user interaction by sending an explicit intent with a malicious filename directly to a share target, potentially triggering an overwrite of critical files.
Assessing the Impact
Microsoft’s investigation pinpointed this vulnerability in several high-profile Android apps, including Xiaomi Inc.’s File Manager and WPS Office, both of which have addressed the issue following Microsoft’s disclosure. The potential impact of this vulnerability varies, with scenarios ranging from manipulation of server settings to execution of malicious code through overwritten native libraries.
Case Study: Xiaomi Inc.’s File Manager
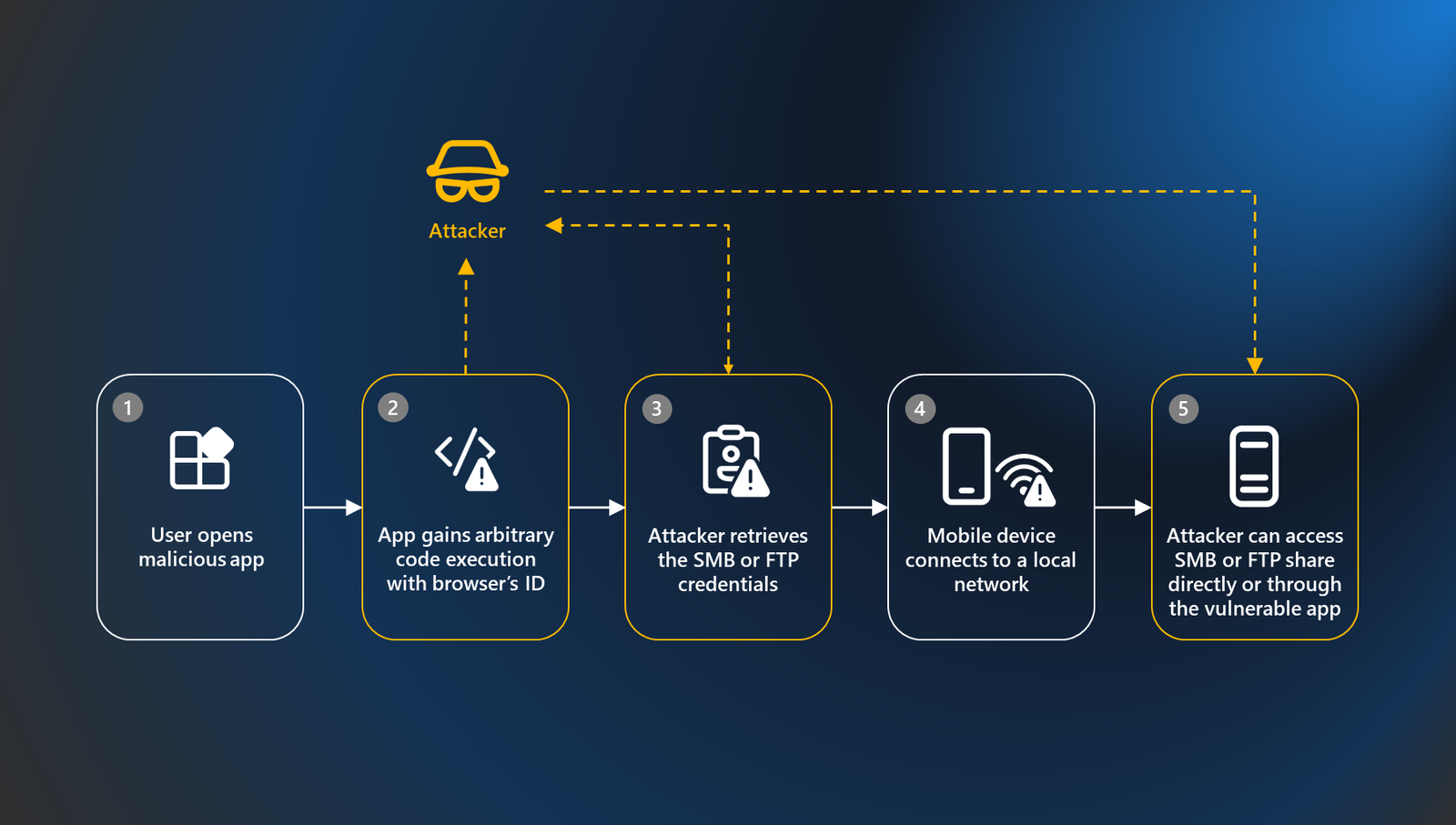
The case study of Xiaomi Inc.’s File Manager, a widely-installed default file manager for Xiaomi devices, illustrates the vulnerability’s potential reach. The app’s permissions and features, such as the ability to connect to remote FTP and SMB shares, underscore the importance of robust security measures. Microsoft’s investigation revealed that the app’s junk files cleaner plugin could be exploited to achieve arbitrary code execution, highlighting the need for vigilance and timely updates.
Addressing the Vulnerability: Findings and Execution
Microsoft’s vulnerability assessment identified the app’s
Understanding the Broader Impact
The exploitation of this vulnerability could have ramifications beyond the user’s device, potentially compromising remote file shares and network security. The case study demonstrates how an attacker could gain access to SMB and FTP credentials and manipulate shared files, underscoring the need for comprehensive security measures.
Guidance for Developers and Users
In response to these findings, Microsoft and Google have provided guidance to help developers avoid such vulnerabilities. Developers are encouraged to use tools like Android Lint and GitHub’s CodeQL to identify potential security issues. For end users, keeping apps updated and installing only from trusted sources is crucial. Microsoft Defender for Endpoint on Android and Microsoft Defender Vulnerability Management offer additional layers of protection against malicious applications and known vulnerabilities.
References and Further Learning
For more insights from Microsoft’s Threat Intelligence community, visit the Microsoft Threat Intelligence Blog and follow their social media channels on LinkedIn and X (formerly Twitter). The Microsoft Threat Intelligence podcast offers additional stories and insights into the evolving threat landscape.