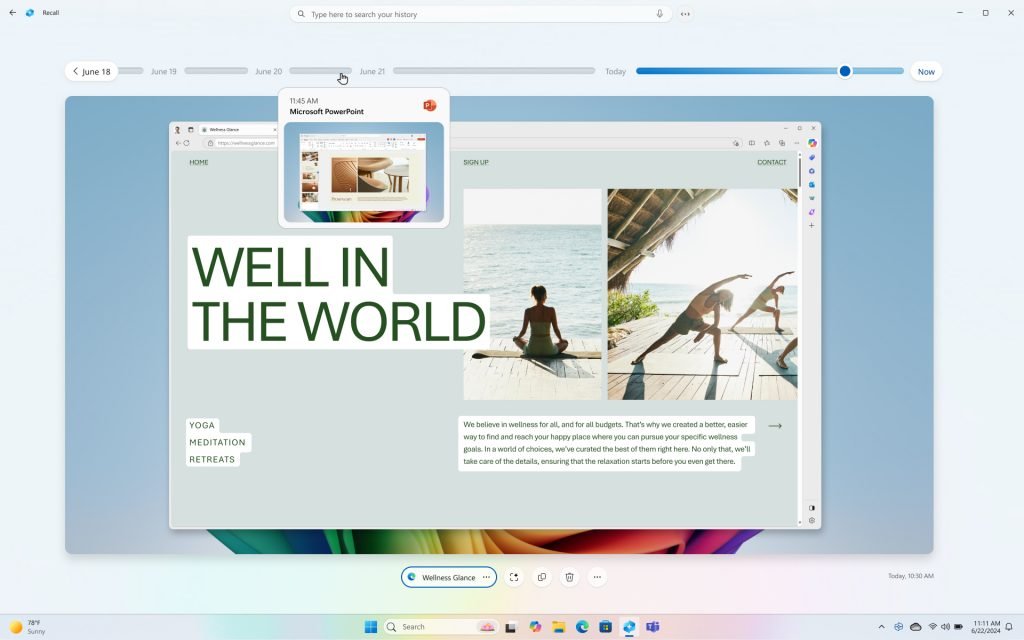
The recent unveiling of Microsoft’s Recall feature for Copilot+ AI PCs has sparked considerable debate within the tech community. Initially designed to allow users to effortlessly locate past activities on their devices, the feature faced immediate backlash due to concerns over its security protocols. Critics highlighted the potential risks associated with the constant screenshotting of user activity, leading to fears about the safety of sensitive information.
Enhanced Security Measures
In response to the swift criticism, Microsoft opted to delay the rollout for Windows Insider beta testers. By June, the company announced a series of enhanced security measures aimed at addressing these concerns. Recall will now be an opt-in feature by default, requiring users to actively enable it during the Windows setup process. Furthermore, the integration of Windows Hello biometric authentication will add an extra layer of security, ensuring that only authorized users can access the Recall database.
Microsoft has emphasized that encryption will be a cornerstone of the Recall experience. The snapshots and associated data will be safeguarded by VBS Enclaves, a software-based trusted execution environment designed to protect sensitive information within host applications. Users will also have the option to completely remove the Recall feature if they choose to do so.
Privacy Controls and User Empowerment
David Weston, Microsoft’s VP of OS and enterprise security, outlined additional protective measures in a recent blog post. He noted that Recall incorporates rate-limiting and anti-hammering strategies to guard against malware threats. While a PIN will serve as a fallback method after Recall is configured, this is intended to prevent data loss in the event of a secure sensor malfunction.
Weston reassured users that privacy remains a top priority, stating, “you are always in control.” By default, Recall will not retain private browsing data across popular browsers such as Edge, Chrome, and Firefox. Additionally, sensitive content filtering will be enabled by default, effectively preventing the storage of critical information like passwords and credit card numbers.
To further bolster confidence in Recall’s security, Microsoft has engaged a third-party vendor to conduct a thorough penetration test and security design review. The Microsoft Offensive Research and Security Engineering team (MORSE) has also been rigorously testing the feature for several months.
Given the rapid and intense backlash, Microsoft’s cautious approach to the Recall rollout is understandable. However, it raises questions about the company’s foresight in anticipating initial criticisms, particularly regarding the accessibility of the Recall database from other local accounts. With the implementation of encryption and additional security measures, these concerns appear to have been addressed, but it leaves one pondering what other oversights may have occurred during the development process.