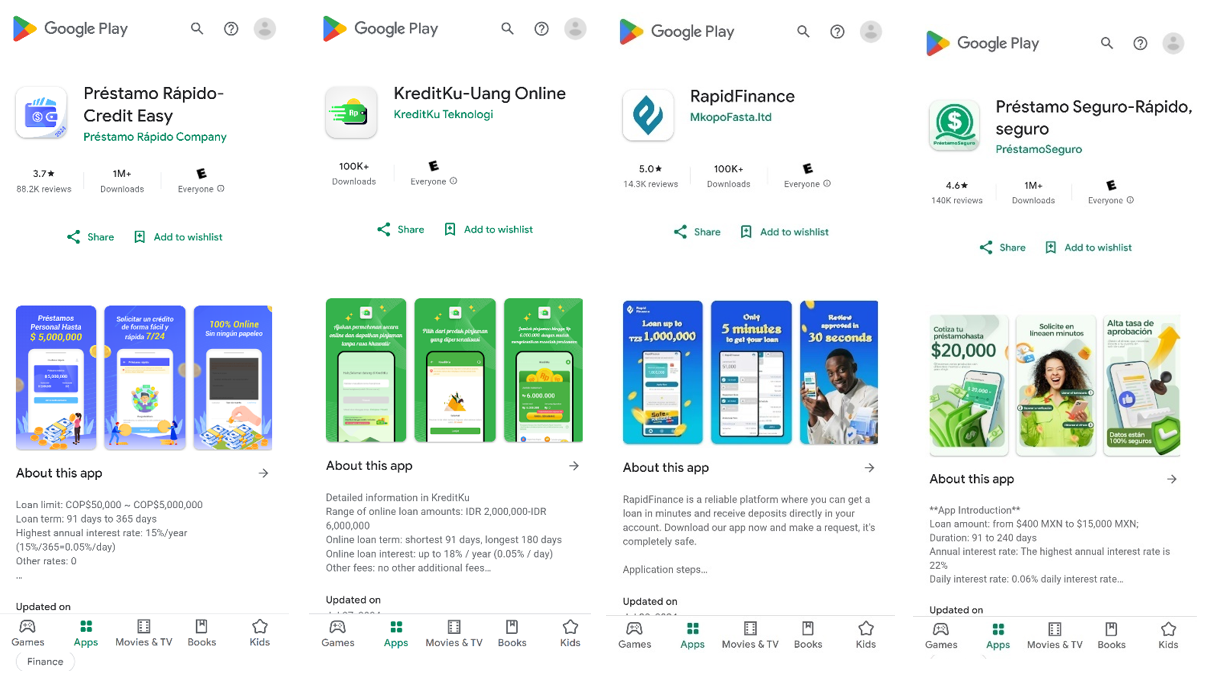
Recent findings by McAfee researchers have unveiled a concerning trend in the realm of mobile applications. A total of 15 SpyLoan Android apps, which have collectively garnered over 8 million installs, were identified on Google Play. These applications primarily target users across South America, Southeast Asia, and Africa.
Exploiting Vulnerabilities
The SpyLoan apps employ social engineering tactics to extract sensitive user information and secure excessive permissions. This often leads to severe consequences such as extortion, harassment, and significant financial losses for unsuspecting users. Many of these malicious applications were promoted through misleading advertisements on various social media platforms.
Upon discovering these threats, McAfee promptly reported the apps to Google. In response, Google notified the developers regarding the violations of Google Play policies. While some of the identified apps were suspended, others were updated by their developers in an attempt to comply with the platform’s regulations.
The prevalence of SpyLoan activity has surged alarmingly, with malicious apps and infected devices increasing by over 75% from the second to the third quarter of 2024. This spike underscores the escalating threat posed by these mobile applications.
According to the report published by McAfee, “SpyLoan apps are intrusive financial applications that lure users with promises of quick and flexible loans, often featuring low rates and minimal requirements. While these apps may seem to offer genuine value, the reality is that they primarily exist to collect as much personal information as possible, which they may exploit to harass and extort users into paying predatory interest rates.” The report further highlights the deceptive marketing strategies employed by these apps, which create a false sense of urgency through time-limited offers and countdowns, ultimately pressuring users into making hasty decisions.
These SpyLoan apps cleverly exploit official app stores like Google Play, utilizing deceptive branding and social media advertisements to appear trustworthy. They often mimic legitimate financial institutions, complete with privacy policies, and employ tactics such as countdown timers and OTP verification to coerce users into divulging sensitive data.
Upon installation, these apps request a range of unnecessary permissions that go far beyond what is required for a loan application. This includes access to contacts, SMS, storage, calendar, phone call records, and even the microphone or camera.
Victims of SpyLoan apps face a myriad of threats, including personal data misuse and harassment. This can manifest in the form of intimidating phone calls, misuse of personal photos or identification, and relentless spamming of contacts, including friends and family.
In a notable incident, authorities in Peru conducted a raid on a call center linked to SpyLoan apps, which had extorted over 7,000 victims across Peru, Mexico, and Chile. Similar scams have been reported globally, indicating a widespread issue.
The report concludes with a stark reminder: “The threat of Android apps like SpyLoan is a global issue that exploits users’ trust and financial desperation. By reusing code and tactics, they can efficiently target different countries, often evading detection by authorities and creating a widespread problem that is difficult to combat.” This networked approach not only amplifies the scale of the threat but also complicates efforts to trace and dismantle these operations, as they can swiftly adapt and relocate their activities to new regions.