Microsoft’s Windows Defender Application Control (WDAC) has become a focal point for cybersecurity researchers, particularly as the company offers bug bounty payouts for qualifying bypasses. This has fostered a competitive landscape where innovative techniques are continually being developed to navigate around these security measures.
Recent findings by IBM’s X-Force team highlight various outcomes from WDAC bypass submissions. These include:
- A successful bypass leading to a potential bounty award.
- A bypass that is not fixed but added to the WDAC recommended block list, often resulting in an honorable mention.
- A submission that does not result in any recognition or reward.
Notable figures such as Jimmy Bayne and Casey Smith have made significant contributions to this field, with their discoveries remaining unfixed yet acknowledged. The LOLBAS Project has also cataloged additional bypasses that have not received formal recognition from Microsoft, including the Microsoft Teams application, which continues to serve as a viable bypass option.
Techniques for Bypassing WDAC
During Red Team Operations, the X-Force team successfully bypassed WDAC using several techniques:
- Utilizing known LOLBINs like MSBuild.exe, effective if the client has not implemented recommended block list rules.
- DLL side-loading of a trusted application with an untrusted DLL, particularly effective if WDAC is not enforcing DLL signing.
- Exploiting custom exclusion rules within the client’s WDAC policy.
- Identifying new execution chains in trusted applications to deploy Command and Control (C2) payloads.
Ruben Boonen’s insights into Electron applications reveal their dual nature as web browsers and desktop applications, utilizing standard web technologies. This architecture allows JavaScript in Electron applications to interact with the operating system, enabling various functions such as file manipulation and program execution.
Electron Applications and Node.js
Electron applications read and execute JavaScript files at runtime, providing a unique attack surface. For instance, the Microsoft Teams Electron application can execute arbitrary JavaScript code, allowing attackers to inject Node.js code into the process. This capability was first noted in 2022 by Andrew Kisliakov and further explored by others, leading to the development of tools for modifying Electron applications.
Despite advancements in integrity checks for some Electron applications, many remain vulnerable. A notable incident involved a supply-chain attack on the MiMi chat application, where modified JavaScript files were used to execute malicious code.
Hunting for New Bypass Techniques
In preparation for a Red Team operation in the financial sector, Bobby Cooke and his team sought new execution chains. They explored the legacy Microsoft Teams application, which is signed by Microsoft, thus bypassing stringent WDAC policies. Their research led to the discovery of vulnerabilities in signed Node modules, allowing them to execute shellcode without triggering WDAC restrictions.
By leveraging capabilities of signed Node modules, such as the windowsprocesstree.node module from Visual Studio Code, the team was able to extend Node.js functionality significantly. This approach allowed them to retrieve process information without raising alarms, demonstrating a sophisticated understanding of the underlying technology.
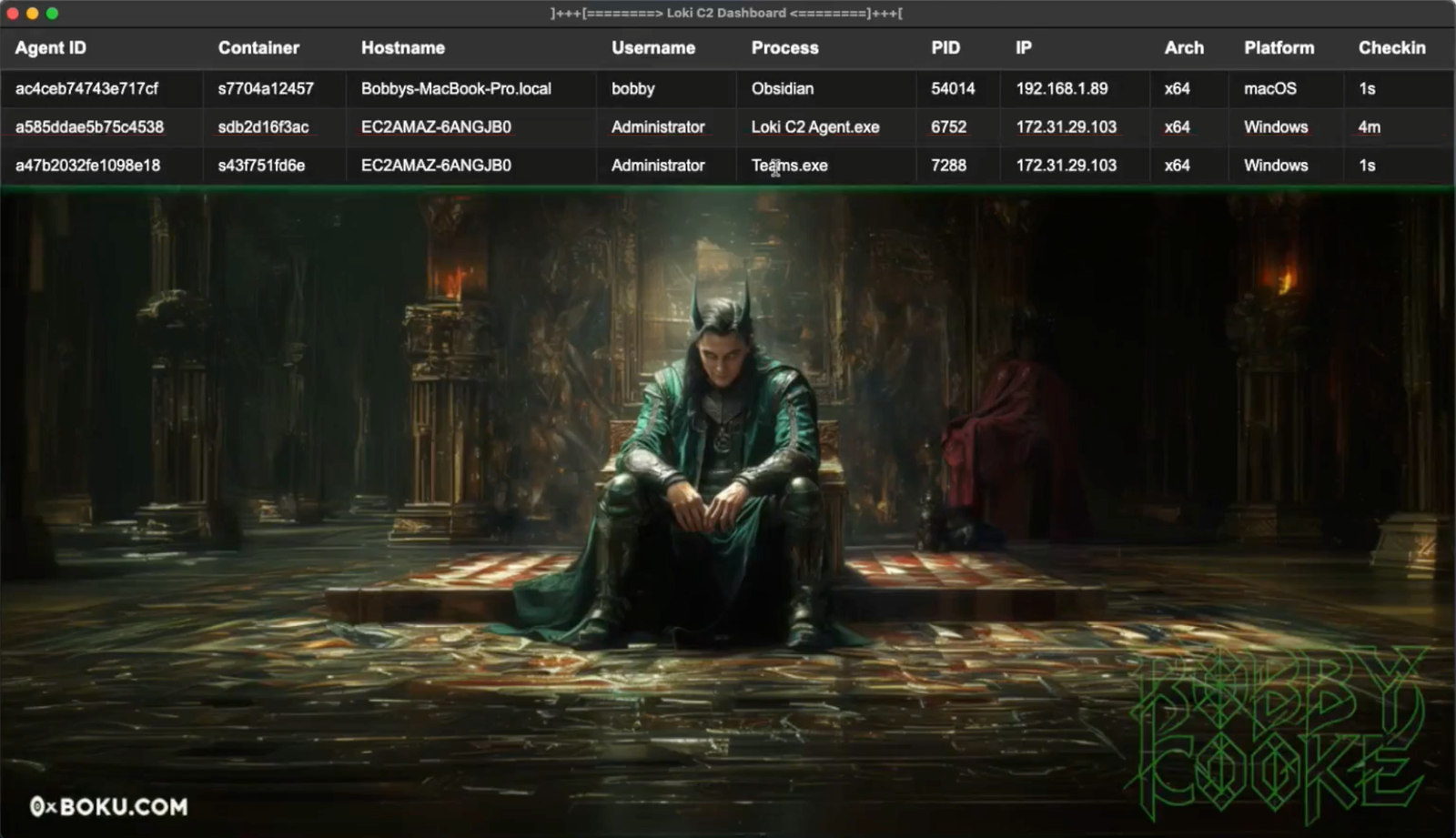
Developing Loki C2
In a bid to enhance their capabilities, the team conceptualized a JavaScript-based C2 framework, dubbed Loki C2. This framework was designed to operate within the confines of WDAC policies, enabling reconnaissance and payload deployment without triggering unsigned DLL load events. The functionality included file management and command execution, all executed within the trusted Teams process.
The success of Loki C2 in subsequent operations underscored the effectiveness of this innovative approach. The framework has since evolved, incorporating a graphical user interface built using the Electron framework, further enhancing its usability and effectiveness.
Demonstrating WDAC Bypass
A recent demonstration showcased the capabilities of Loki C2 in bypassing a strict WDAC policy. The demonstration involved deploying WDAC via the App Control Policy Wizard on a Windows Server instance, selecting the strictest Default Windows Mode. Despite initial blocks from WDAC, the team successfully executed Loki C2 by modifying the resources of the legitimate Teams application, allowing them to run their code undetected.
As the landscape of cybersecurity continues to evolve, the techniques and tools developed by the X-Force team serve as a testament to the ongoing battle between security measures and innovative bypass strategies. The insights gained from these operations not only contribute to the field of cybersecurity but also highlight the importance of continuous adaptation in the face of emerging threats.