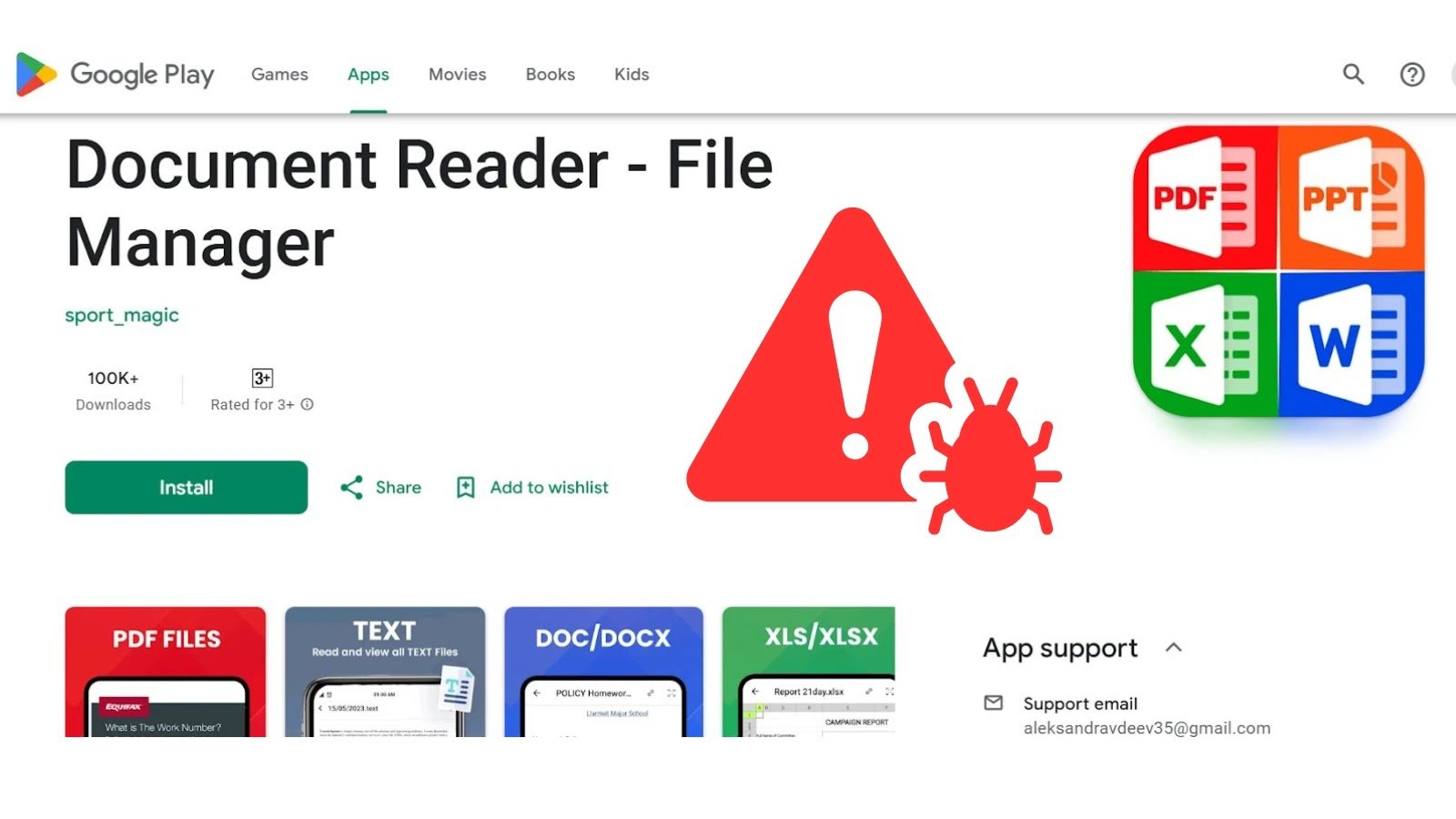
A sophisticated Android banking trojan campaign, known as Anatsa or TeaBot, has made waves in the cybersecurity landscape, amassing over 220,000 downloads on the Google Play Store before its recent removal. This malware is designed to target global financial institutions through a complex, multi-stage infection process, deploying fake login overlays and exploiting accessibility services to pilfer user credentials and execute unauthorized transactions.
Anatsa’s Attack Chain
According to a recent post by Zscaler ThreatLabz shared on X, the malicious application masqueraded as a “File Manager and Document Reader.” This seemingly innocuous app acted as a dropper, retrieving and installing additional payloads from remote servers. Upon installation, users were prompted to download a fraudulent “update,” cleverly disguised as a necessary enhancement, which was actually hosted on GitHub repositories and contained the Anatsa banking trojan.
Anatsa employs reflection-based code execution to dynamically load malicious Dalvik Executable (DEX) files, evading detection by static analysis tools as it decrypts payloads only during runtime. The malware conducts anti-emulation checks to identify sandboxed environments, postponing malicious activities until it confirms the presence of a genuine device. Once activated, it requests critical permissions, including:
- Accessibility Services: To log keystrokes, intercept SMS messages, and manipulate screen content.
- SMS Access: To bypass two-factor authentication (2FA) mechanisms.
Following this, the trojan establishes communication with command-and-control (C2) servers, transmitting device metadata and receiving targeted banking app profiles. For each detected financial application, such as PayPal, HSBC, or Santander, Anatsa injects a counterfeit login overlay, capturing user credentials directly from unsuspecting victims.
The latest campaign has primarily focused on users in Europe, particularly in Slovakia, Slovenia, and Czechia, although its infrastructure is capable of expanding into markets such as the U.S., South Korea, and Singapore. The malware’s target list includes over 600 banking and cryptocurrency applications, allowing threat actors to conduct on-device fraud (ODF) by initiating unauthorized transfers through automated transaction systems (ATS).
Mitigations
To mitigate risks associated with such threats, users are advised to:
- Avoid sideloading: Disable “Install from unknown sources” in device settings.
- Audit app permissions: Revoke accessibility and SMS access for non-essential applications.
- Monitor for updates: Ensure legitimate apps are updated through official stores rather than third-party links.
The Anatsa campaign highlights ongoing vulnerabilities in app store security, particularly regarding delayed payload attacks. While Google has taken steps to remove the identified dropper, similar threats continue to proliferate, often utilizing file managers and utility applications to evade detection.
For end-users, maintaining vigilance and adhering to fundamental security practices remain essential defenses against the evolving landscape of mobile threats.
Indicators of Compromise (IoCs):
Network:
hxxps://docsresearchgroup[.]com
http://37.235.54[.]59/
http://91.215.85[.]55:85
Sample MD5s:
a4973b21e77726a88aca1b57af70cc0a
ed8ea4dc43da437f81bef8d5dc688bdb
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free