Jul 31, 2024Ravie Lakshmanan
Mobile Security / Malware
Malicious Android Apps Target SMS Messages in Global Campaign
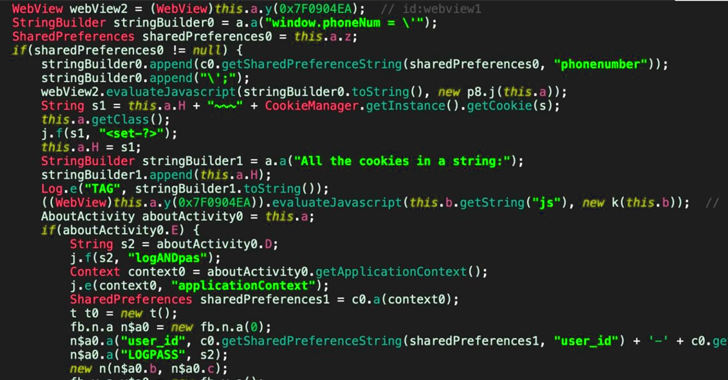
A significant malicious campaign has emerged, leveraging harmful Android applications to pilfer users’ SMS messages since at least February 2022. This extensive operation encompasses over 107,000 unique malware samples, specifically engineered to intercept one-time passwords (OTPs) essential for online account verification, thereby facilitating identity fraud.
According to a report from mobile security firm Zimperium, a staggering 99,000 of these malware applications were previously unknown and not available in commonly accessed repositories. The malware has been observed monitoring OTP messages across more than 600 global brands, some of which boast user bases in the hundreds of millions.
The campaign’s reach is global, affecting victims in 113 countries, with India and Russia leading the list, followed closely by Brazil, Mexico, the United States, Ukraine, Spain, and Turkey.
The initial phase of the attack involves the installation of a malicious app, often facilitated by deceptive advertisements that mimic legitimate Google Play Store listings or through one of the 2,600 Telegram bots that masquerade as trustworthy services, such as Microsoft Word. Once a victim unwittingly installs the app, it requests permission to access incoming SMS messages and subsequently connects to one of 13 command-and-control (C2) servers to relay the stolen messages.
“The malware operates discreetly, continuously monitoring new incoming SMS messages,” researchers noted. “Its primary focus is on OTPs utilized for online account verification.”
The identity of the perpetrators remains unclear, although they have been observed accepting various payment methods, including cryptocurrency, to support a service known as Fast SMS (fastsms[.]su). This service enables customers to purchase access to virtual phone numbers, likely using the numbers associated with infected devices without the owners’ consent to register for various online accounts by harvesting the necessary OTPs for two-factor authentication (2FA).
In early 2022, Trend Micro highlighted a similar financially motivated service that aggregated Android devices into a botnet capable of registering disposable accounts in bulk or creating phone-verified accounts for fraudulent activities.
Zimperium emphasized that these stolen credentials can serve as a launchpad for further fraudulent endeavors, such as creating fake accounts on popular platforms to initiate phishing campaigns or social engineering attacks.
The findings underscore the ongoing exploitation of Telegram, a widely used instant messaging platform with over 950 million monthly active users, by malicious actors for various purposes, including malware distribution and command-and-control operations.
Recently, Positive Technologies unveiled two families of SMS stealers, dubbed SMS Webpro and NotifySmsStealer, targeting Android users in Bangladesh, India, and Indonesia, with the intent of siphoning messages to a Telegram bot controlled by the threat actors. Additionally, the Russian cybersecurity firm identified malware strains masquerading as TrueCaller and ICICI Bank, capable of exfiltrating users’ photos, device information, and notifications via the messaging platform.
Security researcher Varvara Akhapkina noted, “The chain of infection typically begins with a phishing attack on WhatsApp,” where attackers often employ phishing sites posing as banks to lure users into downloading malicious apps.
Another malware variant utilizing Telegram as a C2 server is TgRAT, a Windows remote access trojan that has recently been updated to include a Linux variant. This malware is equipped to download files, capture screenshots, and execute commands remotely.
Doctor Web remarked on the widespread use of Telegram as a corporate messenger, stating, “It is not surprising that threat actors can exploit it as a vector to deliver malware and steal confidential information, given the program’s popularity and the routine traffic to Telegram’s servers, which facilitates the camouflage of malware on compromised networks.”
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.