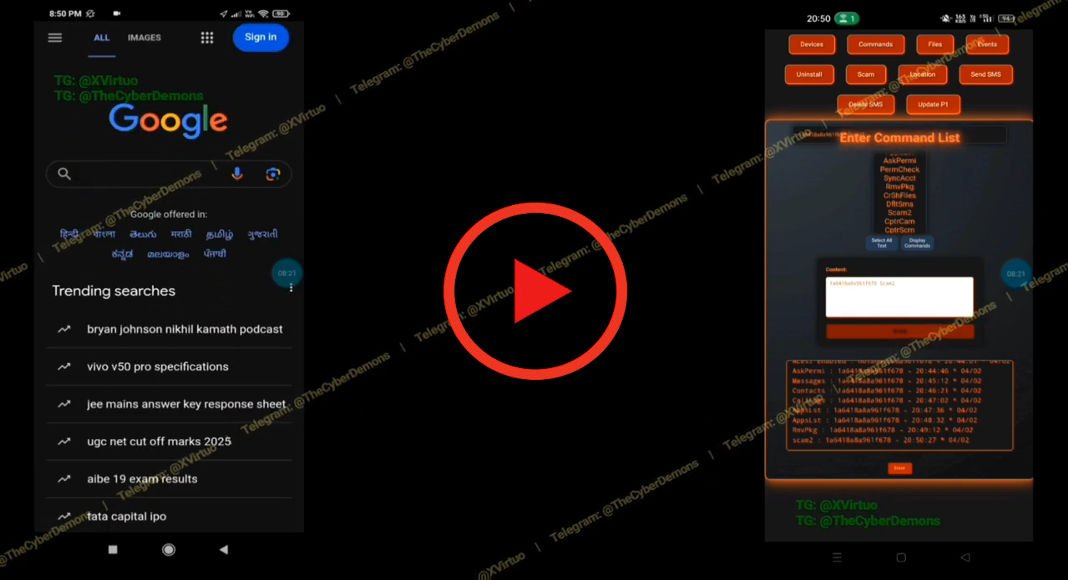
A new Android Remote Access Trojan (RAT) has emerged on GitHub, touted as fully undetectable, prompting significant alarm among cybersecurity experts. This sophisticated malware claims to circumvent advanced permission and background process restrictions, particularly in customized Chinese ROMs like MIUI and EMUI, marking it as one of the most formidable public threats to Android security observed to date.
With a focus on persistence, encrypted communication, and evasion of antivirus detection, researchers caution that this RAT could catalyze a surge in ransomware and credential-stealing attacks.
Advanced Injection and Permission Evasion
The RAT employs a multi-layer dropper that integrates its malicious payload within legitimate Android applications, tricking users into installing compromised APKs. Unlike traditional RATs, it is specifically designed to overcome autostart restrictions, background app controls, and aggressive battery optimization features prevalent in custom Android ROMs.
Upon installation, the RAT stealthily escalates its privileges, automatically granting itself comprehensive accessibility, notification, and administrative rights through controlled script execution. This effectively undermines the user permission model, allowing for covert operations immediately following infection.
Encryption is central to its functionality. The command-and-control (C2) communication utilizes AES-128-CBC encryption with PKCS padding, safeguarding all transmitted data from scrutiny, even under deep packet inspection. The developer’s documentation indicates that the configuration, including the C2 address, is thoroughly obfuscated, thwarting exposure during APK decompilation or reverse-engineering attempts.
Additionally, an anti-emulator module checks hardware parameters before execution, preventing the RAT from operating within sandbox environments typically used by analysts.
Full Device Compromise and Surveillance Capability
Once activated, the RAT achieves complete control over the device, mirroring the capabilities of commercial-grade spyware. It can record and delete call logs, initiate or intercept voice calls, and manipulate SMS messages, including reading one-time passwords (OTPs) and spoofing sender information.
Equipped with a built-in keylogger, the malware captures every keystroke, targeting credentials from banking applications, cryptocurrency wallets, email clients, and two-factor authentication tools. It also features multiple data exfiltration capabilities, such as live screen captures, access to both front and rear cameras, audio and video recording, and clipboard hijacking, which can replace cryptocurrency wallet addresses with those belonging to the attacker.
The ransomware aspect of the malware further amplifies its threat by encrypting files across storage partitions and locking the device interface until a ransom is paid. The attacker retains the ability to remotely lock, unlock, or even wipe the entire device, transforming the RAT from a mere surveillance tool into a potentially destructive payload.
Moreover, the inclusion of spoofed notifications, cloned application login pages, and automated phishing prompts adds a layer of social engineering to the infection chain, facilitating real-time credential theft.
Persistence, Stealth, and Public Exposure
The RAT’s persistence mechanisms are meticulously crafted for longevity. It operates with minimal system resource usage, running a background process that consumes negligible CPU and battery power. In “freeze mode,” its network traffic is reduced to under 3MB per day, making detection by network monitors exceedingly challenging. Hidden icons and delayed task scheduling further mitigate user suspicion, while deceptive system dialogs are employed to crash security applications and Play Protect manually.
Perhaps most concerning is its accessibility: the attacker interface is entirely web-based, requiring no specialized infrastructure or port forwarding. An operator can execute full control commands from any standard browser across Android, Linux, or Windows devices.
By making such a potent toolkit freely available online, the developers have significantly lowered the barrier to entry for conducting industrial-grade mobile espionage operations. The public release of this fully undetectable Android RAT highlights the increasing misuse of open-source repositories for distributing weaponized tools.
In response, security analysts are calling for the immediate removal of the project and greater scrutiny over malware publishing on platforms like GitHub to prevent further exploitation of Android devices on a global scale.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates