Researchers from HUMAN’s Satori Threat Intelligence and Research Team have made a significant discovery in the realm of digital advertising fraud, unveiling a widespread operation dubbed “SlopAds.” This intricate scheme utilizes 224 Android applications, which have collectively amassed over 38 million downloads across 228 countries and territories. The primary objective of SlopAds is to deploy fraud modules that stealthily siphon ad revenue on a massive scale.
What sets SlopAds apart is its sophisticated multi-layered obfuscation strategy. This approach activates only when installations stem from ad campaigns orchestrated by the threat actors themselves, thereby minimizing the digital footprint left for forensic analysis.
Upon being installed through non-organic means, each SlopAds application connects to Firebase Remote Config to retrieve an encrypted configuration. This configuration cleverly conceals URLs for four PNG images that contain fragments of an APK, cleverly hidden using digital steganography.
Once these images are reassembled on the device, they reconstruct the core fraud component known as FatModule. Prior to this reconstruction, the app conducts a mobile marketing attribution check, exploiting legitimate attribution tags to confirm that the installation resulted from a tracked ad click. This ensures that only organically installed instances appear benign, effectively diverting any scrutiny.
Advanced Evasion and Fraud Mechanisms Drive 2.3 Billion Daily Bid Requests
Once FatModule is operational, SlopAds employs robust anti-analysis measures. The module is programmed to abort execution if it detects any debugging tools, emulated environments, or rooted devices. Furthermore, all strings within the app and the FatModule itself remain encrypted, while native Java code is packed to obscure its functionality at first glance. These counter-reverse-engineering tactics significantly impede sandboxing and static analysis efforts.
After passing these checks, SlopAds applications initiate hidden WebViews to gather device fingerprinting data, user-agent strings, browser attributes, and rooting indicators. This information is relayed to the command and control (C2) server, which then selects high-value targets for further exploitation.
Validated devices receive instructions to navigate through multiple H5 cash-out domains owned by the threat actors. Each domain is designed to redirect several times, sanitizing referrer headers and disguising the traffic’s origin. Within these hidden WebViews, the domains host game or news sites programmed to display viewable ads and execute automated clicks at precise coordinates and timings, mimicking genuine user engagement and achieving impressive fill and click-through rates.
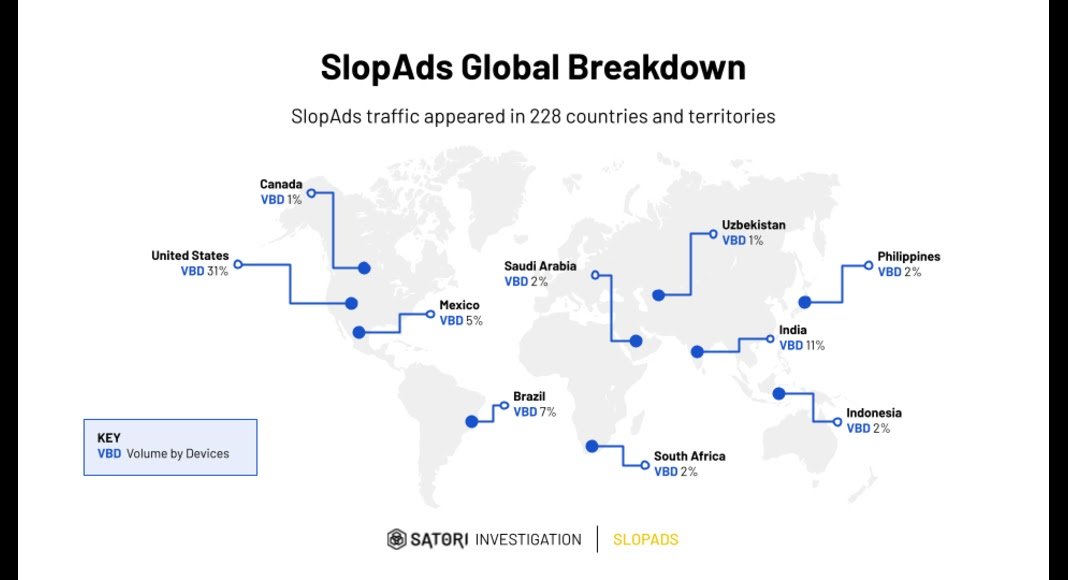
At its peak, SlopAds was responsible for generating approximately 2.3 billion bid requests daily, with traffic predominantly concentrated in the United States (30%), India (10%), and Brazil (7%). The extensive C2 infrastructure and over 300 promotional domains funnel users to SlopAds applications, highlighting the threat actors’ ability to scale their operations effectively.
In response to this threat, Google Play Protect automatically alerts users and blocks known SlopAds applications during installation. Additionally, Google has removed all identified packages from the Play Store. However, users who have installed these applications from off-market sources remain vulnerable until they manually uninstall the affected apps.
For customers utilizing HUMAN’s Ad Fraud Defense and Ad Click Defense solutions, protection against SlopAds’ sophisticated tactics is assured. Meanwhile, Satori researchers continue to monitor newly staged applications and evolving fraud modules to stay ahead of adversary adaptations, thereby safeguarding the integrity of the digital advertising ecosystem.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates