Recent findings from IMDEA Networks Institute reveal a troubling practice involving Facebook and Instagram apps that have been covertly tracking Android users’ web browsing activities without their consent. This tracking mechanism circumvents Android’s privacy controls and operates even in incognito mode, impacting millions of websites that incorporate Meta’s tracking code. Notably, Russian tech giant Yandex has employed similar techniques since 2017, creating a vast cross-platform surveillance network that connects users’ mobile identities with their online behaviors across billions of devices globally.
The Hidden Localhost Backdoor
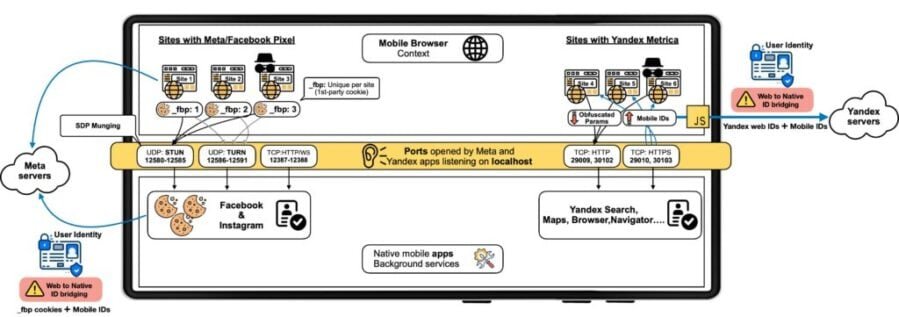
The tracking exploits a lesser-known aspect of Android’s permission system. Upon installation, Facebook and Instagram apps establish background services that listen on designated network ports, akin to secret frequencies capturing data from web browsers on the same device. The process unfolds as follows: when Android users access websites featuring Meta’s tracking pixel, JavaScript code discreetly transmits their browsing cookies through localhost connections to any Facebook or Instagram apps operating in the background. These apps then associate the web activity with users’ logged-in accounts and send the enriched data back to Meta’s servers.
Aniketh Girish, a PhD student at IMDEA Networks and co-author of the research, elaborates, “What’s interesting here is where the bridging happens and how it allows these trackers to de-anonymize users’ mobile web traffic. In the case of Meta’s Pixel, it uses localhost channels to share browser identifiers via WebRTC with their native apps like Facebook or Instagram, where the data is linked to the user’s logged-in account and quietly relayed to Meta’s servers by the app.”
Yandex’s More Sophisticated Approach
Yandex adopts an even more invasive strategy. The Russian company’s applications—including Maps, Navigator, Browser, and Search—utilize what researchers describe as a “command-and-control” system reminiscent of malware behavior. Nipuna Weerasekara, another researcher on the team, remarks, “What surprised me most was the dynamic nature of Yandex apps using the AppMetrica SDK. Yandex implements this tracking method in a way that resembles command-and-control nodes in malware, retrieving listening port configurations and start-up delays from Yandex servers at runtime.”
Yandex apps delay the activation of their tracking capabilities for up to three days post-installation, a tactic believed to be designed to avoid detection.
Scale of the Surveillance
The extent of this tracking is remarkable. Meta’s pixel is present on approximately 5.8 million websites, while Yandex Metrica is embedded in around 3 million sites. This means the tracking could potentially affect billions of Android users visiting these sites. Testing across the top 100,000 websites revealed that about 78% of sites with Meta’s pixel attempted localhost communications without explicit user consent, while for Yandex, the figure reached 84%.
What Makes This Different
This method of tracking diverges from traditional web tracking that browsers can block, functioning instead at the operating system level. It remains effective regardless of whether users:
- Clear their cookies or browsing data
- Utilize incognito or private browsing modes
- Are not logged into Facebook or Instagram in their browser
- Have disabled location tracking or other privacy settings
This tracking undermines Android’s built-in privacy protections, as it does not depend on conventional web cookies or browser storage that users can manage.
The Malicious App Risk
Of particular concern is the potential for malicious apps to exploit this technique to eavesdrop on users’ complete browsing histories. Researchers have created a proof-of-concept app illustrating how any malicious application could listen on the same ports and gather real-time data on users’ website visits. Yandex’s use of unencrypted HTTP requests, unlike Meta’s more sophisticated WebRTC approach, allows any app monitoring the required ports to track which websites users visit, effectively compiling a comprehensive browsing history accessible to third-party applications.
Website Owners Left in the Dark
Evidence suggests that many website operators integrating these tracking tools were unaware of the localhost communications. Developer forums reveal confusion among website owners questioning why Meta’s pixel was connecting to local ports, with complaints surfacing as early as September 2024. One developer expressed frustration in forum posts, stating, “No acknowledgment has come from Meta at all on this though. My support request with them got a generic response and then ignored thereafter.” Neither Meta nor Yandex has documented these tracking capabilities in their official developer resources.
Browser Vendors Fight Back
In response to the researchers’ findings, major browser vendors are implementing countermeasures. Chrome version 137, released in late May 2025, introduces specific protections against these tracking methods, blocking the exploited ports and disabling the SDP munging technique that Meta used to obscure data transfers. Other browsers are following suit, although these fixes only address the current implementation. As research leader Narseo Vallina-Rodriguez notes, “The fundamental issue enabling this attack is the lack of control over local host communications on most modern platforms.”
Interestingly, Meta’s tracking ceased on June 3rd, coinciding with the public release of the research. The researchers commented, “We don’t know why Facebook stopped using this technique on the day of our public release, but we’re pleased to see that Android users are no longer affected by this type of abuse after our disclosure (for now).”
A Broader Platform Problem
This research underscores a significant security gap in how mobile platforms manage localhost communications. Vallina-Rodriguez emphasizes, “Technical mitigations should not disrupt legitimate usages of localhost sockets like anti-fraud or authentication methods, so it is necessary to complement any technical solution with stricter platform policies and store vetting processes to limit abuse.”
Until comprehensive platform-level solutions are implemented, the only surefire protection for Android users is to avoid Facebook, Instagram, and the affected Yandex applications altogether—a drastic measure that underscores how this tracking technique compromises user choice and consent within the digital landscape.
Fuel Independent Science Reporting: Make a Difference Today
If our reporting has informed or inspired you, please consider making a donation. Every contribution, no matter the size, empowers us to continue delivering accurate, engaging, and trustworthy science and medical news. Independent journalism requires time, effort, and resources—your support ensures we can keep uncovering the stories that matter most to you. Join us in making knowledge accessible and impactful. Thank you for standing with us!